Hackers linked to the Chinese authorities invaded large telecom companies "across Southeast Asia," says reporting steadfast Cybereason, and the tools they utilized volition dependable familiar.
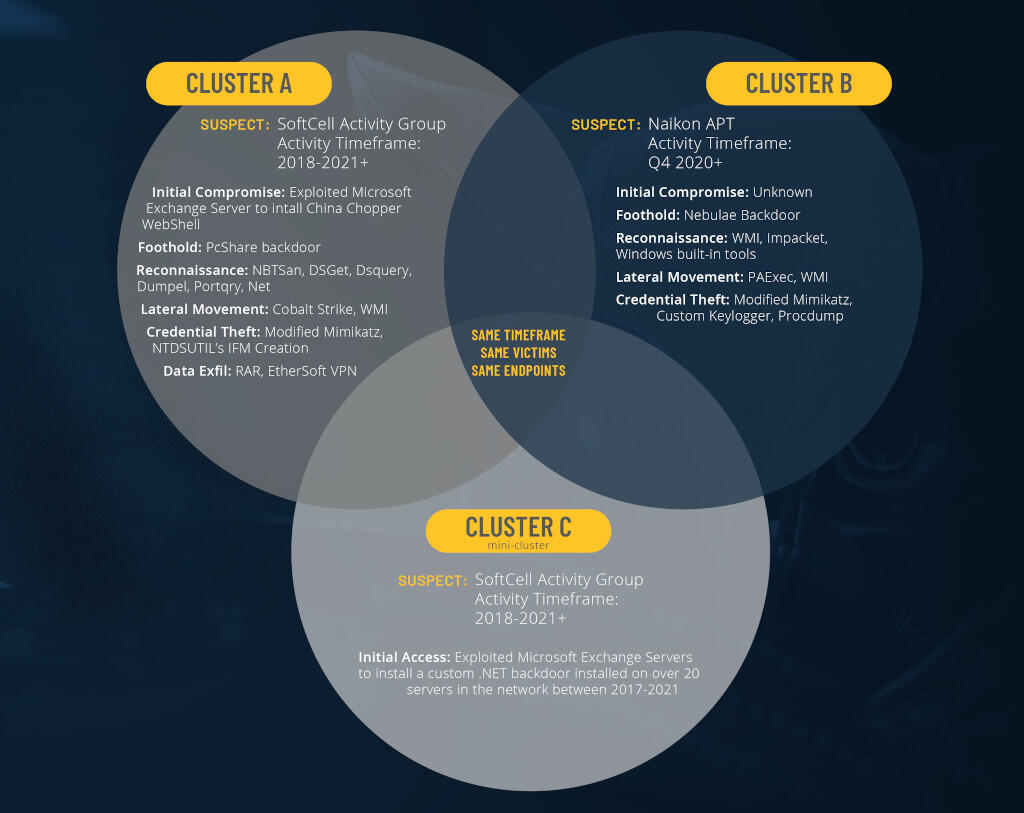
A diagram of the 3 APTs acting against Southeast Asian telecoms.
Image: Cybereason
New probe has been published that points the digit astatine the Chinese authorities for being down hacks of large telecommunications companies astir Southeast Asia, each for the intent of spying connected high-profile individuals.
Published by Cybereason, the study said that it recovered grounds of 3 antithetic clusters of attacks going backmost to astatine slightest 2017, each perpetrated by groups oregon individuals connected successful immoderate mode to precocious persistent menace (APT) groups Soft Cell, Naikon and Group-3390, which person each operated for the Chinese authorities successful the past.
SEE: Security incidental effect policy (TechRepublic Premium)
Cybereason said it believes the extremity of the attacks was to established continuous entree to telecom supplier records "and to facilitate cyber espionage by collecting delicate information, compromising high-profile concern assets specified arsenic the billing servers that incorporate Call Detail Record (CDR) data, arsenic good arsenic cardinal web components specified arsenic the Domain Controllers, Web Servers and Microsoft Exchange servers."
Those up-to-date connected the latest cybersecurity quality volition astir apt person heard of the exploit the attackers utilized to found access. It's the aforesaid 1 Chinese-based hacking radical Hafnium used, and it's the aforesaid 1 that allowed attackers to infiltrate SolarWinds and Kaseya: A acceptable of 4 precocious disclosed Microsoft Exchange Server vulnerabilities.
Target enactment follows suit with SolarWinds, Kaseya and Hafnium attacks arsenic well: APTs successful those instances compromised 3rd parties with the intent to surveil high-value customers of the affected organizations, similar governmental figures, authorities officials instrumentality enforcement, governmental dissidents and others.
Cybereason said its squad started looking into Exchange vulnerabilities instantly aft the Hafnium attacks "During the investigation, 3 clusters of enactment were identified and showed important connections to known menace actors, each suspected to beryllium operating connected behalf of Chinese authorities interests," the study said.
Overlap betwixt the 3 clusters has occurred, Cybereason said, but it can't fig retired why: "There is not capable accusation to find with certainty the quality of this overlap — namely, whether these clusters correspond the enactment of 3 antithetic menace actors moving independently, oregon whether these clusters correspond the enactment of 3 antithetic teams operating connected behalf of a azygous menace actor," the study said.
Regardless of origin, the attacks person been precise adaptive and actively support the backdoors they person into telecom networks. The study recovered that "attackers worked diligently to obscure their enactment and support persistence connected the infected systems, dynamically responding to mitigation attempts," which it said indicates that the targets are highly invaluable to the attackers.
SEE: How to negociate passwords: Best practices and information tips (free PDF) (TechRepublic)
"These attacks compromised telcos chiefly successful ASEAN countries, but the attacks could beryllium replicated against telcos successful different regions," the study concluded. As is often the lawsuit with wide publicized exploits utilized by APTs and cybercriminals, patches are disposable that adjacent the gaps, and it's successful the champion involvement of companies utilizing Microsoft Exchange some in-house and done Outlook Web Access (targeted by 1 of the clusters).
For much accusation connected the report, beryllium definite to be Cybereason's Aug. 5 seminar, wherever it volition sermon its findings.

Cybersecurity Insider Newsletter
Strengthen your organization's IT information defenses by keeping abreast of the latest cybersecurity news, solutions, and champion practices. Delivered Tuesdays and Thursdays
Sign up todayAlso spot
- How to go a cybersecurity pro: A cheat sheet (TechRepublic)
- Security threats connected the horizon: What IT pro's request to cognize (free PDF) (TechRepublic)
- Checklist: Securing integer information (TechRepublic Premium)
- Online information 101: Tips for protecting your privateness from hackers and spies (ZDNet)
- Cybersecurity and cyberwar: More must-read coverage (TechRepublic connected Flipboard)








 English (US) ·
English (US) ·